🕵️♂️ What Is the Hidden Wiki in 2025?
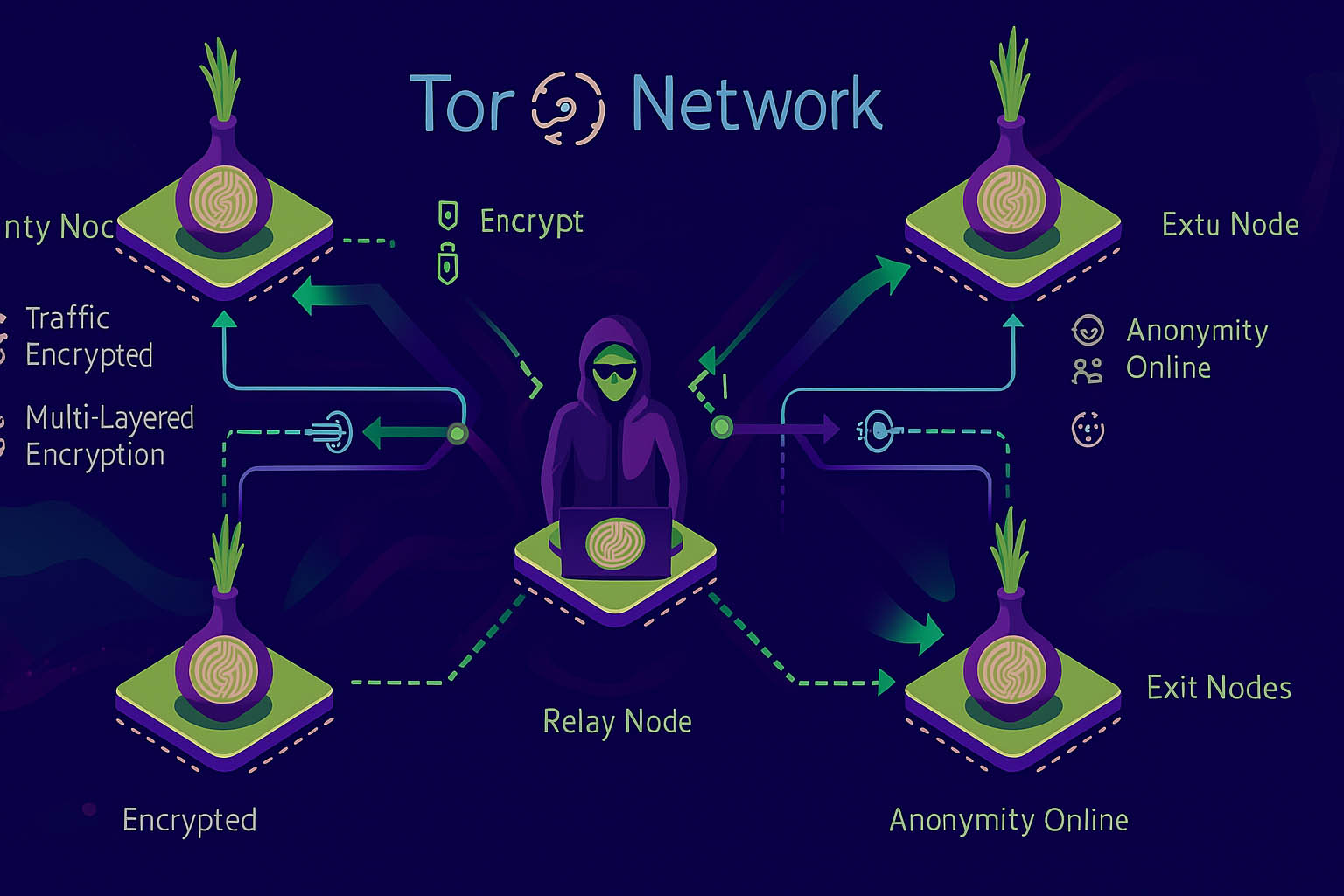
How It Works – Overview of Onion Addresses and Tor Browsing
In 2025, ensuring safe access to the Hidden Wiki is essential for avoiding scams and fake links while browsing the dark web. The Hidden Wiki is not a single fixed website but rather a collection of .onion links hosted on the Tor network. In 2025, it will still serve as one of the most recognized entry points to the dark web. To access it, you must use the Tor Browser, which routes your internet traffic through multiple encrypted nodes. This layered routing obscures your IP address, making it extremely difficult for anyone to track your online activity.
Deep Web user experiences in 2024.
Onion addresses are unique in that they end with “.onion” instead of common extensions like .com or .org. These addresses are generated using cryptographic keys and are not indexed by traditional search engines like Google. Each onion address is a long string of random characters, which makes them resistant to domain hijacking but also harder to remember. For this reason, directories like the Hidden Wiki are essential — they act as a central hub where users can find verified onion sites.
Why It’s Popular – Gateway Role for Dark Web Newcomers
The Hidden Wiki’s popularity comes from its directory-style structure. For newcomers to the dark web, finding legitimate onion sites can be overwhelming and risky. The Hidden Wiki simplifies this by grouping sites into categories, such as forums, marketplaces, email providers, and news outlets. This makes navigation easier while reducing the risk of stumbling onto malicious or illegal sites.
In 2025, its role has expanded beyond just being a link list. Many versions of the Hidden Wiki now include security tips, PGP verification guides, and uptime checks for listed links. However, because the dark web is constantly evolving, many fake or malicious clones mimic the real Hidden Wiki. This makes knowing how to find a trusted version absolutely essential for anyone wanting to browse safely.
📜 The Evolution of the Hidden Wiki
Early Versions vs. 2025 Updates
The earliest versions of the Hidden Wiki appeared in the mid-to-late 2000s, not long after the Tor network became publicly available. Back then, the design was extremely basic — a plain wiki-style page listing onion sites, many of which were experimental or short-lived. There was little focus on security or link verification, and dead links were common.
Over the years, as interest in the dark web grew, so did the demand for reliable link directories. By 2015, some versions of the Hidden Wiki began including categories for news, whistleblowing platforms, privacy tools, and marketplaces. Still, verification was minimal, and phishing scams were rampant.
What the Hidden Wiki is in 2025
Fast forward to 2025, and modern Hidden Wiki versions have evolved significantly. Many now feature uptime monitoring, PGP signature verification, last-checked dates, and warnings for risky categories. The design has become more user-friendly, and some versions even provide guides for Tor beginners, making it easier to browse without falling into obvious traps.
Why So Many Clones Exist
The Hidden Wiki’s popularity has made it a prime target for imitation. Creating a clone is relatively easy — all someone needs is a basic Tor hosting setup and a list of onion addresses. Malicious operators often create these clones to spread phishing links, install malware, or trick users into revealing sensitive information.
In other cases, clones are created for legitimate purposes — for example, to provide a mirror that stays online if the main version is taken down. However, the challenge for users is telling the difference between a safe mirror and a dangerous fake. This is why relying on verified sources and cross-checking onion addresses is essential when accessing the Hidden Wiki in 2025.
⚠️ Common Risks When Accessing the Hidden Wiki
Fake Mirrors and Clones – How Scammers Replicate the Site
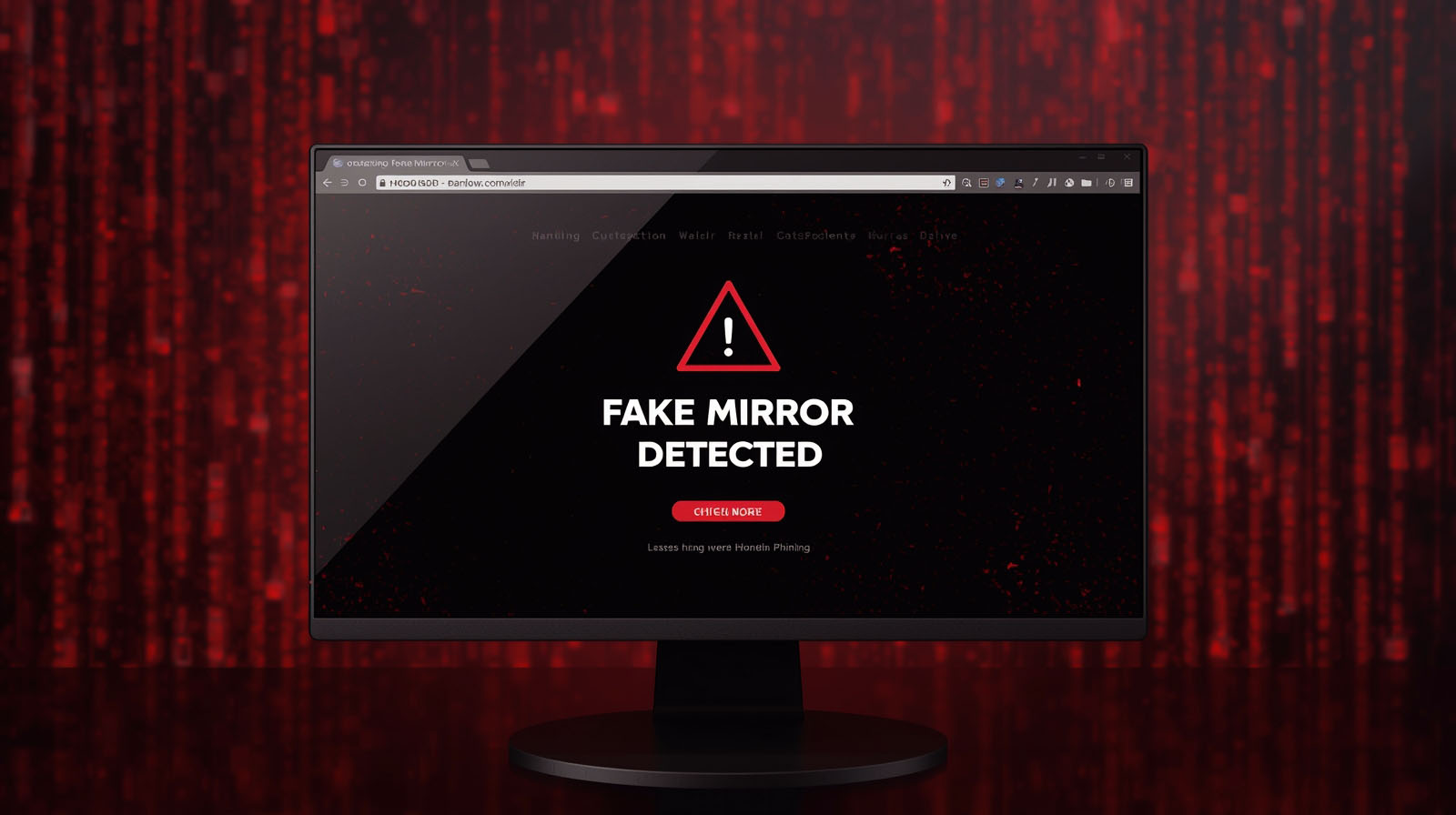
One of the most common dangers when visiting the Hidden Wiki in 2025 is stumbling onto a fake mirror. Scammers can easily create a page that looks identical to the real Hidden Wiki — complete with similar categories, familiar link lists, and even copied descriptions. They then swap out legitimate onion addresses for malicious ones.
These cloned versions often appear on forums, in social media posts, or even in search results on privacy-focused search engines. The problem is that onion URLs are long, random strings, making it difficult for users to notice if a single character has been altered. A fake mirror might redirect you to a phishing site, a scam marketplace, or even a page designed to collect your personal information.
Because of this, you should only use verified onion links from trusted sources, and ideally, check them against PGP-signed announcements from the site operators.
Dangerous Links – Phishing, Malware, and Illegal Content
Even on the genuine Hidden Wiki, not every link is safe. Some categories contain phishing sites that mimic popular marketplaces or services, luring you into entering login credentials or cryptocurrency wallet keys. Others may link to pages that host malicious downloads — files disguised as helpful tools but containing spyware, ransomware, or keyloggers.
There’s also the risk of stumbling onto illegal content, which can lead to severe legal consequences depending on your jurisdiction. In many cases, these sites intentionally disguise their true nature to get more clicks from unsuspecting users.
For this reason, safe browsing habits are essential. Disable scripts in Tor Browser, avoid downloading unknown files, and never interact with suspicious marketplaces or services. Remember: A single careless click on the dark web can compromise your security.
🛡 How to Safely Access the Hidden Wiki
Use Verified Onion Links – Importance of Trusted Sources
The safest way to access the Hidden Wiki in 2025 is by starting with verified onion links from reputable sources. Since onion URLs are a long, random mix of letters and numbers, spotting a fake one can be nearly impossible without verification. That’s why you should only get Hidden Wiki links from places with a track record of reliability, such as established privacy communities, well-known onion indexes like DarkFail, or official announcements from trusted Tor-based services.
When you find a Hidden Wiki link, compare it with other reputable sources to ensure it matches exactly. Even a single character difference can mean you’re on a completely different — and potentially dangerous — website. Bookmark trusted onion links once you confirm they are correct, so you don’t have to search for them repeatedly.
Check PGP Signatures & Last-Checked Dates
Many legitimate Hidden Wiki versions now display PGP signatures alongside their URLs. A PGP (Pretty Good Privacy) signature is a cryptographic verification that ensures a third party hasn’t altered the link. By checking this signature against the site’s public key — often listed on forums like Dread or the Tor Project’s own site — you can confirm that the link is authentic.
Equally important are last-checked dates. Onion links tend to go offline or change frequently, so an updated Hidden Wiki will show when each link was last verified to be online. Outdated directories are riskier because they may contain dead links that scammers later reuse for malicious purposes.
Test Links in a Sandbox or Virtual Machine First
If you want an extra layer of safety, open new onion links inside a sandboxed environment or a virtual machine (VM). A VM is an isolated operating system running inside your main computer, meaning even if malware infects it, your real device stays safe. Tools like VirtualBox or Qubes OS make this process easier.
For the most cautious users, running Tor on a dedicated system such as Tails OS or Whonix provides maximum protection. This ensures that even if you land on a compromised site, your real IP address, personal files, and main operating system remain untouched.
🚫 Avoiding Scams and Fake Links
Spotting Suspicious URLs – Typos, Odd Characters, Mismatched Mirrors
One of the easiest ways scammers trick users on the dark web is by creating lookalike onion addresses. Since onion URLs are long strings of random letters and numbers, a single character change is easy to miss. These altered links — sometimes called “typosquats” — often lead to phishing pages or malware-infected sites.
Pay attention to small differences. For example, the real onion address might have “abc123” in the middle, while the fake one swaps it for “abc12q.” Also, be wary of sites claiming to be the “official” Hidden Wiki but having mismatched designs or categories compared to other trusted mirrors.
If you find multiple versions of the same site with slightly different addresses, check them against known verified sources before clicking.
Using Onion Search Engines for Safer Discovery (Ahmia, DarkFail)
Rather than relying solely on random forum posts or social media to find onion links, use trusted onion search engines like Ahmia and DarkFail.
-
Ahmia works both on the clearnet and Tor, filtering out known scam sites.
-
DarkFail specializes in tracking official onion addresses for popular sites and lists verified mirrors.
By using these services, you reduce the risk of stumbling across dangerous or fake versions of the Hidden Wiki and other dark web resources.
Avoiding Too-Good-to-Be-True Marketplace Claims
Scammers prey on curiosity and greed. You might encounter links promising “huge discounts” on high-demand items, “untraceable” services, or “exclusive” access to rare products. On the dark web, these kinds of offers are often pure scams designed to steal your cryptocurrency or personal data.
If a marketplace claims to be “the new Silk Road” or offers suspiciously low prices, treat it with extreme caution. Even if the site looks legitimate, it could be a short-term scam that disappears after taking users’ money.
The safest approach is to stick to established marketplaces with verified onion addresses, and even then, exercise caution with every transaction.
🔐 Privacy Tools for Hidden Wiki Browsing
Tor Browser Security Settings – Safe Mode, JavaScript Control
The Tor Browser is your gateway to the Hidden Wiki, but it’s only as secure as the settings you choose. In 2025, one of the first things you should do is set Tor Browser to “Safest” mode. This setting disables most scripts, certain fonts, and potentially risky media formats that can be used for tracking or delivering malicious code.
Another critical step is controlling JavaScript. While JavaScript can make web pages interactive, it’s also a common attack vector on the dark web. By default, “Safest” mode disables most JavaScript functions, but you can manually review and block any that slip through using Tor’s built-in controls or an extension like NoScript. You can explore the EFF’s online privacy guide for practical tips on maintaining anonymity while browsing onion sites.
Why a VPN Is Recommended Before Tor
Although Tor hides your IP address by routing traffic through multiple nodes, your internet service provider (ISP) can still see that you’re connecting to the Tor network. This could raise suspicion in certain countries. By using a VPN before Tor (often called “Tor over VPN”), you hide your Tor usage from your ISP and add another encryption layer.
A VPN also protects you if a Tor entry node is compromised, ensuring your real IP remains hidden. The key is to choose a no-logs VPN provider that doesn’t store your activity and supports strong encryption standards.
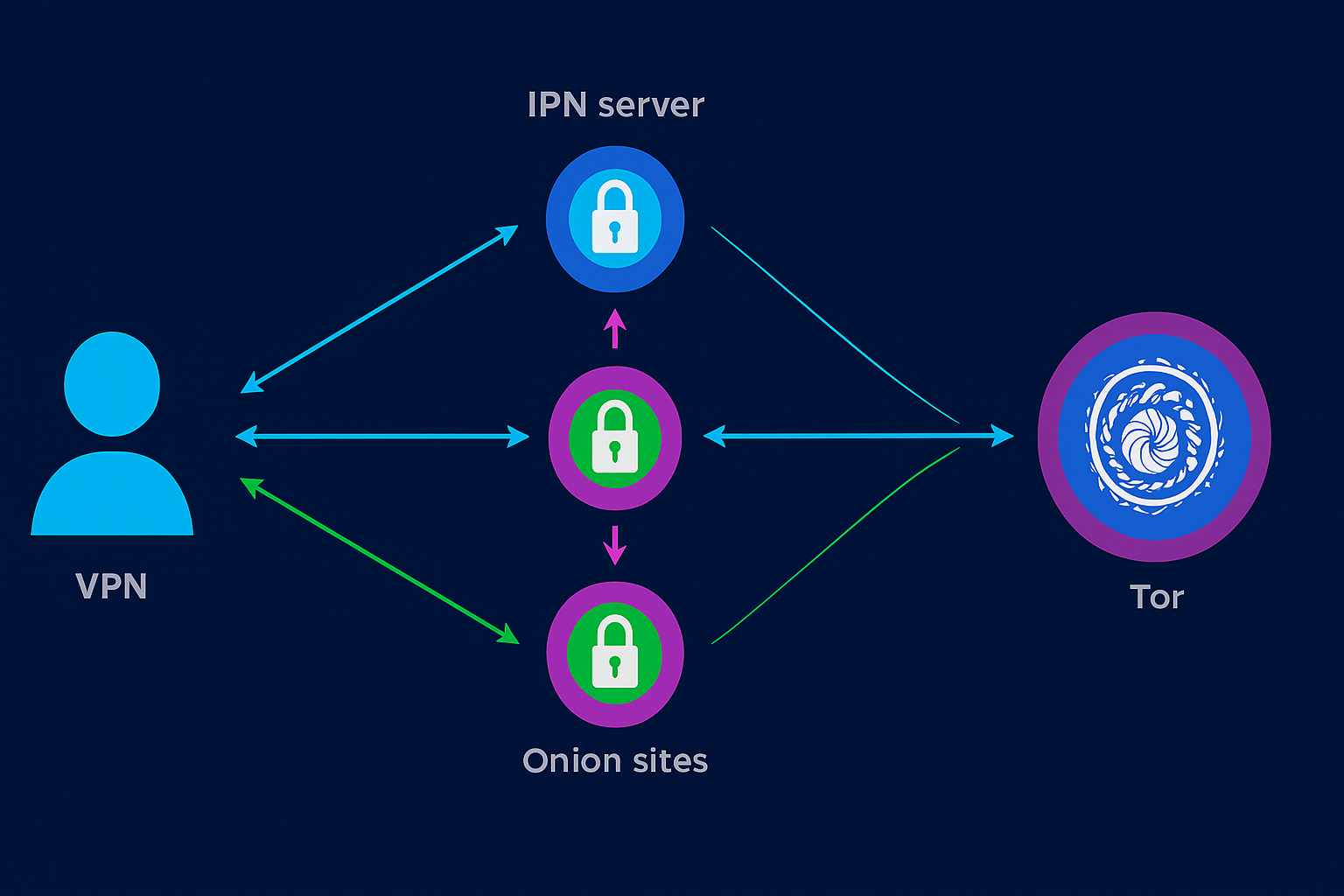
Secure Operating Systems (Tails, Whonix)
For maximum security while browsing the Hidden Wiki, consider using privacy-focused operating systems like Tails or Whonix. For an even stronger layer of anonymity, the Whonix privacy-focused OS routes all traffic through Tor by default.
-
Tails is a live OS that runs from a USB stick and leaves no trace on your computer once you shut it down. It routes all connections through Tor automatically.
-
Whonix uses a two-part system: one virtual machine acts as a Tor gateway, and the other is for everyday browsing. This separation adds a strong layer of isolation between you and potential threats.
These secure environments reduce the risk of malware infections, data leaks, and tracking attempts. For anyone who frequently visits onion sites, combining Tor, a VPN, and a privacy OS is the safest browsing strategy in 2025.
⚖️ Legal Considerations When Using the Hidden Wiki
Are Onion Links Legal in Your Country?
The legality of accessing onion links varies depending on your country’s laws. In most jurisdictions, simply visiting the Hidden Wiki or other onion-based sites is not illegal as long as you are not engaging in prohibited activities. For example, browsing a news outlet or a whistleblowing platform on the dark web is generally lawful in many democratic nations.
However, some countries — particularly those with strict internet censorship — may classify the use of Tor or the dark web itself as suspicious or even unlawful. Nations like China, Iran, and North Korea have heavy restrictions, and connecting to Tor could trigger government monitoring or legal action.
It’s also important to remember that while the Hidden Wiki can list perfectly legal onion sites, it can also link to illegal services and content. Accessing or interacting with such material can lead to severe criminal charges, even if you didn’t intend to engage in wrongdoing.
How to Stay Within Legal Boundaries
To use the Hidden Wiki safely and legally in 2025, always focus on legitimate, non-criminal content. Stick to categories that clearly offer lawful resources, such as:
-
Privacy tools and encrypted email services.
-
Dark web versions of reputable news outlets.
-
Forums and communities that discuss technology, security, and anonymity.
Avoid clicking on anything that promises illegal goods, hacking services, or prohibited content. Even if you’re “just looking,” in many countries, intent is not required for certain charges — the act of accessing banned material can be enough to violate the law.
If you live in a country with ambiguous or restrictive online laws, using a VPN in combination with Tor can provide some protection from ISP logging or surveillance. However, a VPN is not a license to break the law — it simply reduces exposure to monitoring.
By understanding your country’s legal stance and staying disciplined with your browsing habits, you can explore the Hidden Wiki without risking legal trouble.
🌐 Trusted Alternatives to the Hidden Wiki
DarkFail – Verified Mirror Listings
DarkFail is one of the most reliable resources for finding official onion mirrors. It was created to help users avoid phishing scams and malicious clones. Instead of hosting random links, DarkFail focuses on verifying each listed site through PGP-signed proofs from the operators themselves.
Its interface is simple. You’ll find a list of popular onion services, each with its last-known working address, uptime status, and signature verification. This means you can confirm that a link is authentic before you click on it. The archived .onion resources available at the Internet Archive offer historical snapshots of dark web directories and forums.
One advantage of DarkFail is its focus on safety. It avoids linking to marketplaces known for scams and prioritizes sites with a trustworthy track record. The site is available both as an onion address and a clearnet version, making it easy to check before you open Tor.
For Hidden Wiki users, DarkFail is a great companion resource. You can cross-check links from the Hidden Wiki against DarkFail’s verified list to reduce your chances of landing on a fake site.
Ahmia – Clearnet and Onion Search Engine
Ahmia is another trusted alternative, but instead of a static directory, it’s a search engine for the Tor network. It works on both the clearnet and Tor, which means you can look up onion addresses without directly connecting to the dark web.
Ahmia filters out sites hosting illegal content, so results tend to be safer compared to random forum recommendations. It’s especially useful for discovering new sites that may not be listed on the Hidden Wiki or DarkFail.
Each result includes a short description, and some have uptime data, helping you find active links faster. You can also search for keywords like “encrypted email” or “dark web news” to get category-specific results.
For anyone who values safety and accuracy, combining Ahmia’s search capabilities with DarkFail’s verified listings provides a much more secure browsing experience than relying on the Hidden Wiki alone.
Other Onion Directories That Passed Security Checks
While the Hidden Wiki is well-known, there are other onion directories that have proven to be safer and more reliable. These platforms go through security vetting to ensure they don’t host obvious scams or dangerous links.
One example is OnionLinks, which organizes verified onion sites into clear categories. It focuses on uptime monitoring and removes inactive addresses quickly.
Another is The Tor Directory, a smaller but carefully maintained list of trusted sites. It often includes niche resources that don’t appear on larger indexes.
Some privacy-focused communities also host private link collections shared only among verified members. These lists are updated regularly and often tested for phishing or malware threats before being shared.
Using multiple trusted directories instead of relying on a single source reduces the risk of landing on a malicious site. Cross-checking links between these directories is one of the best ways to stay safe on the dark web.

📝 Final Thoughts – Safe & Responsible Dark Web Use
Bookmarking Trusted Sources for Future Access
Once you’ve found safe and verified onion links, it’s best to bookmark them for future use. This avoids having to search again, which reduces your chances of stumbling onto a fake or malicious mirror.
If you use the Tor Browser, keep bookmarks organized in folders, such as “News,” “Privacy Tools,” or “Directories.” This way, you can quickly find what you need without visiting unverified sources.
It’s also a good idea to keep an offline backup of important onion addresses in an encrypted file or password manager. If a site goes offline temporarily, having the correct URL saved will help you confirm when it comes back online.
Ethical and Legal Considerations
Browsing the dark web can be done safely and legally — but only if you stick to lawful and ethical content. Avoid marketplaces that deal in illegal goods, hacking services, or any site that promotes criminal activity.
Always remember that in many countries, intent doesn’t matter when it comes to certain offenses. Simply accessing prohibited content can result in serious consequences.
If you’re in a region with strict internet monitoring, use a VPN before Tor to help shield your activity from your ISP. However, even with strong privacy tools, it’s your responsibility to ensure your browsing habits remain within the law.
By combining security best practices, legal awareness, and ethical browsing, you can explore the Hidden Wiki and other dark web resources without putting yourself or your data at unnecessary risk.